I revised the title many times. Am I giving the impact breadth of what it could be without veering into click-bait?
Bluetooth Low Energy MESH Network, it is built into the OS without any noted country exemption. Although there be will many air gaps, that is not what I mean.
Some questions that came to mind reading it?
- Can China even pull it out of the OS for good measure, hack it?
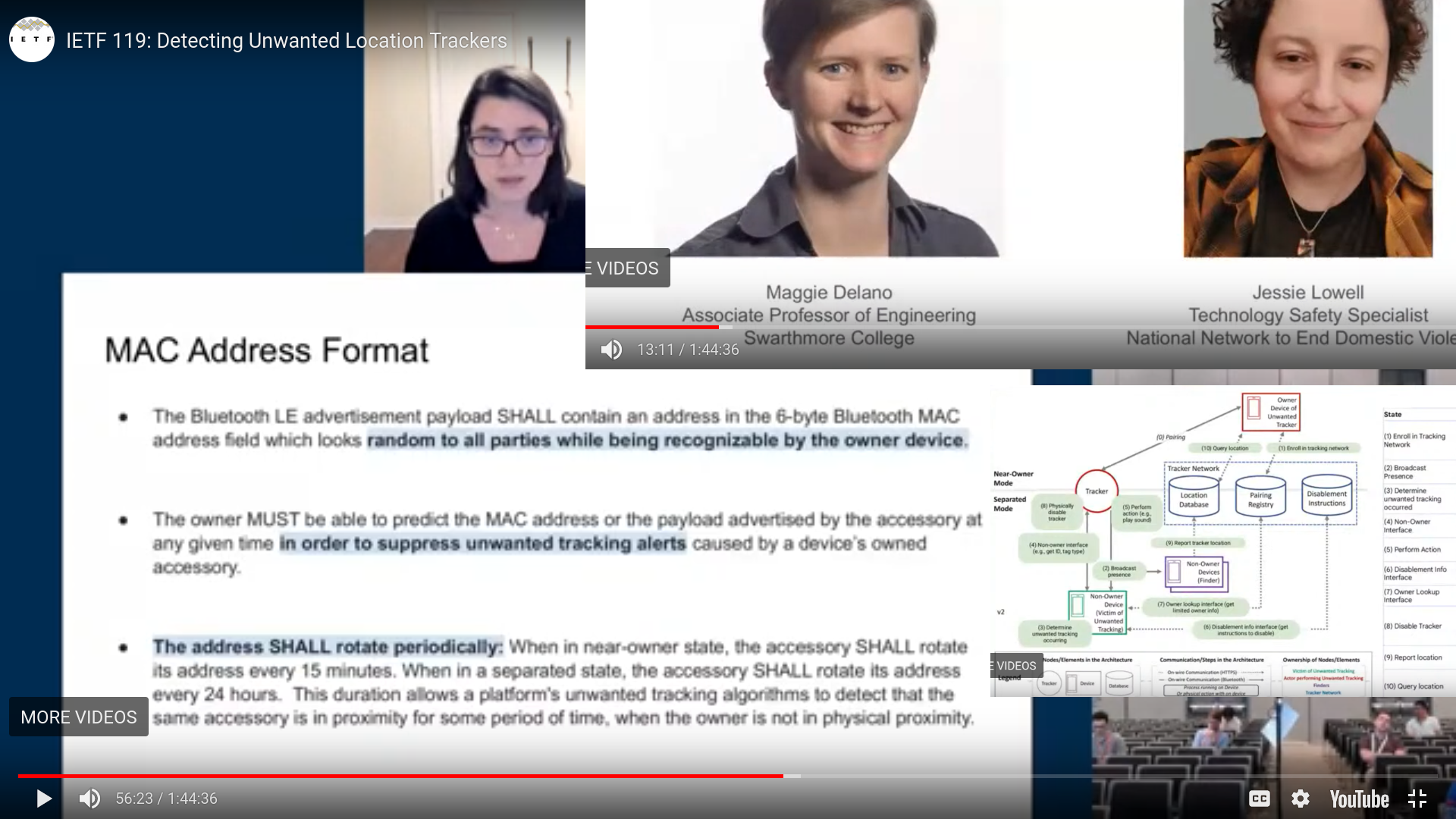
- Even with topology of some enable, others disable, others wanting security will be reading bluetooth MAC addresses of un-consenting, disabled, for tracking of others whom have enabled, even if they are not being targeted. See below screenshots from the Internet Engineering Task Force presentation.
- Is the Bluetooth freqz and combinatory fields bio-active in any regard of it's function? Do plants stay healthy around "high intake" Bluetooth whatever that may be?
- They mentioned other devices and Industry being involved, how many devices to we expect to also use this protocol in the future?
- If we mapped it out, all of these devices thus operating, mapped out of the whole network with a Supercomputer, real-time, how much energy do you think it would be? How many BLE pulses per second, in a busy metropolitan area?
- Who pushed for this TRACKING NETWORK I will be partcipating in whether I like or NOT (uptake)?
- Where was the pre-planning market and socio-economic research on this presented beforehand?
- If entities very intent on tracking you, will just disable/refuse the protcol, then why instead would Apple and Alphabet whom introduced the vulnerability, just ...make thier own implementation secure?
So we're going to skip this useless marketing-speak on 9to5 Mac - Here’s how the new Cross-Platform Tracking Detection works in iOS 17.5
As far as I can tell, there is nothing that says it doesn't perform assessment of the MAC address in range, all of them, for "your" security of course. In fact, it seems in line with what they want to accomplish: Track all the trackers? Later safeguard them with a "Safefilter" online database check when Phone starts?
Did I get it wrong?




Canva is on the traditional corp Extend, Embrace, Extinguish mission to snuff Digital Content Design that is local only and has no AI. Canva bought Affinity Design Suite, which was the reaction of the non-corp creative world to not have to Adobe Creative Cloud, may it burn.
I believe we are in the era of "the great rug pull" of consumer empowered technology, moving to corp empowered technology stack, with them in control at all levels.