thankfully that is a special mailbox for spam, I sometimes like to come through the emails and see where they submit the data, and maybe submit some data on my own, plus report the issue to website owner/hosting
moira
At my instance I did setup a email wildcard (receive emails from any address on that domain which don't already have a account) and I get a lot of phishing and scam emails, most of them are send "to" /c/[email protected], as link to this community is linked in sidebar, but I also seen emails "send to" random usernames
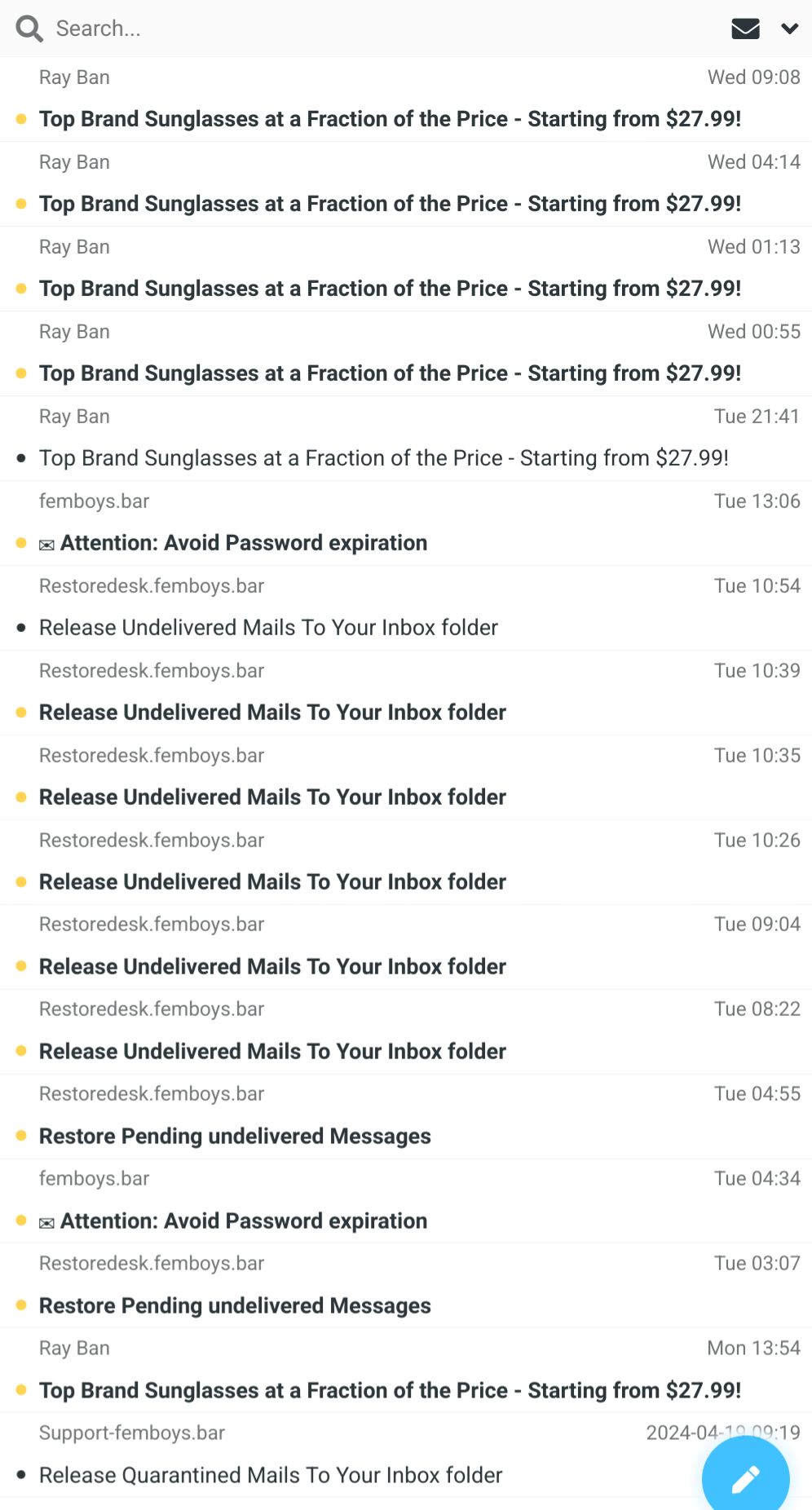
So yeah, It is happening, i wonder how bad it is on larger instances
you can play on multiplayer just fine, as long as server have enabled offline-mode
For minecraft you can just use a offline mode in pretty much every 3rd party launcher, like SKLauncher
i miss old plex (~2016), when it was actually focused on providing local content, good thing jellyfin exist
I doubt it was a real wallet - most likely it was just a scam exchange that would prompt you to send cryptocurrency "for verification" before you could try to withdraw them.
The idea was already exploited on prnt.sc, where it is possible to try bruteforce screenshot ID and find other users public screenshots - https://splashdot.github.io/scam1/

It doesn't matter that website loads javascript code for logged in user, as you need a token (which server will give you after a successful login) to authenticate to apis, it is pretty common to do that way
There wasn't a client side API, but the API was missing crucial validation of user input (eg only checking the mac address but didn't check who is actually authenticated)